Not all pretenders are Open source... this is true with zimbra at least which claims it is open source but actually I see everythg they r doing is against open source. check this for detailed discussion abt zimbra as open source.
I am still in my battle field working on Zimbra.
We upgraded to the new zimbra version now....
In this new version I found sthg in the code that made my nerves; all variables are written in this format "_158", "_140".
I found this hilarious...
About Me
- Ahmed Abd-ElHaffiez Hussein
- PhD Candidate at Purdue University, Computer Science.
Sunday, July 22, 2007
Saturday, June 30, 2007
The fall of MS fan
For most of life, I have been a Microsoft user. I wasn't a MS' fan. But I didn't find it was not so bad working on Window, and it was fair enough for me, although it is not perfect.
I had great passion to try the Vista out, the long delayed version, 6 years or sthg. We all read abt it for many years, and how much it will be sthg fascinating and a new..bla..bla..bla
When I tried it on my PC, i was expecting sthg that could dazzle me.
finally, I got Vista business. I was totally wrong, I regret the day i installed Vista.
well, it is beautiful, the 3-D desktop switcher looks nice.
I faced many many problems with Drivers. the problem is not that they r not verified by Vista. the problem that from time to time, I had to redefine the drivers.
my network card kept me to be disconnected. I couldn't stay online for couple of hours. the stupid thing that when it disconnects, i have to press by myself "diagnose and repair" then should also "get IP" to ask the Vista to get another IP. What is this stupidity!!! didn't I define that already in the connection properties!! the answer to that question is the "ALLOW" :))
If u run sthg on vista, and precipitate away from ur PC, don't expect it is working.
u should wait because u will have to answer "Continue with getting a new IP?", "continue with opening this executable file"..etc I really hate this stupid thg in vista. i don't think i have to press 3 clickes just to run exe file..
The gadgets are terrible, I have never turned them on. they are not innovative and poor.
fighting to have a network connection really annoyed me.
this Vista eats the processor and the Memory. it slows down ur PC. without any tasks running ur RAM usage can be 512 MB. to use a PC now. u have to add $X o buy extra RAM for the Vista beast and $Y extra to more powerful processor, don't forget that u will pay for the Vista too :)
it seems to me that Vista price is too high. despite the license price is the almost the same since many old versions of windows, it is too high comparing with HW costs these days. Windows license can exceed 20% of ur costs!!!!
the only thg that may keep windows alive is that majority of mobile tools need windows to sync, and some softwares are not still available for MACs.
anyways, I didn't like the Vista thg.
I had great passion to try the Vista out, the long delayed version, 6 years or sthg. We all read abt it for many years, and how much it will be sthg fascinating and a new..bla..bla..bla
When I tried it on my PC, i was expecting sthg that could dazzle me.
finally, I got Vista business. I was totally wrong, I regret the day i installed Vista.
well, it is beautiful, the 3-D desktop switcher looks nice.
I faced many many problems with Drivers. the problem is not that they r not verified by Vista. the problem that from time to time, I had to redefine the drivers.
my network card kept me to be disconnected. I couldn't stay online for couple of hours. the stupid thing that when it disconnects, i have to press by myself "diagnose and repair" then should also "get IP" to ask the Vista to get another IP. What is this stupidity!!! didn't I define that already in the connection properties!! the answer to that question is the "ALLOW" :))
If u run sthg on vista, and precipitate away from ur PC, don't expect it is working.
u should wait because u will have to answer "Continue with getting a new IP?", "continue with opening this executable file"..etc I really hate this stupid thg in vista. i don't think i have to press 3 clickes just to run exe file..
The gadgets are terrible, I have never turned them on. they are not innovative and poor.
fighting to have a network connection really annoyed me.
this Vista eats the processor and the Memory. it slows down ur PC. without any tasks running ur RAM usage can be 512 MB. to use a PC now. u have to add $X o buy extra RAM for the Vista beast and $Y extra to more powerful processor, don't forget that u will pay for the Vista too :)
it seems to me that Vista price is too high. despite the license price is the almost the same since many old versions of windows, it is too high comparing with HW costs these days. Windows license can exceed 20% of ur costs!!!!
the only thg that may keep windows alive is that majority of mobile tools need windows to sync, and some softwares are not still available for MACs.
anyways, I didn't like the Vista thg.
Wednesday, June 27, 2007
My Writely Document
I used frequently these days my writely dcocument to share docs with friends. It is nice, I was just installing my windows and I didn't have my openOffice running. Writely helped me to start writing without bothering on installing any office.
but I noticed some problem with it.
If u copy from openOffice and paste in ur writely document, the numbering will be abused in some cases.
Also, if u face a problem with connection, and while disconnection another buddy is updating the Doc, u may have a trouble when ur connection is back.
u will try to refresh to check if anybody has updated the doc while u r offline. the problem is u won't get anythg by refreshing. so, u will think nobody updated anythg.
What is happenning is that when u come back online, the writely will consider ur old version is the most recent update and replace any changes happened while offline. if u didn't put this in consideration u will work on ur old version and didn't get ur buddy's updates.
to get ur buddy's work u have check the revision by urself, and if u find that some work has done while u r offline , click revert to the version preceding the last one.
but I noticed some problem with it.
If u copy from openOffice and paste in ur writely document, the numbering will be abused in some cases.
Also, if u face a problem with connection, and while disconnection another buddy is updating the Doc, u may have a trouble when ur connection is back.
u will try to refresh to check if anybody has updated the doc while u r offline. the problem is u won't get anythg by refreshing. so, u will think nobody updated anythg.
What is happenning is that when u come back online, the writely will consider ur old version is the most recent update and replace any changes happened while offline. if u didn't put this in consideration u will work on ur old version and didn't get ur buddy's updates.
to get ur buddy's work u have check the revision by urself, and if u find that some work has done while u r offline , click revert to the version preceding the last one.
Thursday, June 07, 2007
Erlang Vs Object Oriented
I think that in the future the functional programming community will be at peak. currently I think that the functional communities are too small to beat the Java community.
the functional is easier to any person. any one can write a functional code. Erlang for example has a light VM that can make profit of multiprocessors availability. this doesn't depend on certain compiler that enables parallelism in Java or C.
if you don't care about performance, think about parallelism as simpler way to structure software in a domain where there is a lot of natural concurrency.
I read a paper "Structured Programming Using Processes" in which the author tried to prove that the Erlang was capable to support a personal accounting software application. Maybe you can take a look to it later.
also, I like to point to Yaws, Yaws is a HTTP high performance 1.1 webserver particularly well suited for dynamic-content webapplications. I ma really amazed by its performance.
well, but why Erlang is not widely used till now?
Well the world likes Java. the type safe language. Security in distributed Erlang is “all or nothing,” so when a node is authenticated to another, it can perform any operation.
process isolation is not complete, a process can flood another process with messages, or it can steal all the CPU cycles by entering into an infinite loop.
the functional is easier to any person. any one can write a functional code. Erlang for example has a light VM that can make profit of multiprocessors availability. this doesn't depend on certain compiler that enables parallelism in Java or C.
if you don't care about performance, think about parallelism as simpler way to structure software in a domain where there is a lot of natural concurrency.
I read a paper "Structured Programming Using Processes" in which the author tried to prove that the Erlang was capable to support a personal accounting software application. Maybe you can take a look to it later.
also, I like to point to Yaws, Yaws is a HTTP high performance 1.1 webserver particularly well suited for dynamic-content webapplications. I ma really amazed by its performance.
well, but why Erlang is not widely used till now?
Well the world likes Java. the type safe language. Security in distributed Erlang is “all or nothing,” so when a node is authenticated to another, it can perform any operation.
process isolation is not complete, a process can flood another process with messages, or it can steal all the CPU cycles by entering into an infinite loop.
Thursday, May 24, 2007
Agile Process
My first reading about Agile was the Agile Manifesto. I think this was enough to get the whole picture of the agile philosophy.
I really don't recommend that you get a book to read about the agility; it will be a contradiction to read a book as long as the Agile methods emphasize working software as the primary measure of progress. It is better you spend the time understanding your working environment and maturity to apply the best process that can fit with it.
I lived a similar experience with eSpace when they were aiming to get a CMM certificate, CMMI or whatever they will call it after couple of years.I think that finally the people here got the good decision by putting this plan away, and put their own standards, the standards best fitting with their teams and their environment. I doubt their was a need to some white collar guy to supervise our documents and our working styles to decide whether we fit to Mr XYZ standards or not. I also got the chance to meet some guys from another company having this certificate. What I found is that they modified their hierarchical structure just to accommodate the standard although their team wasn't capable at all to support this hierarchy.
Anyway, let's move to another point...
When we talk about the agile process we should identify very well any possible limitations before adopting it. It is very clear for me that it needs mature people, and this can be considered as one of the limitations.
Another factor that may limit the agile adoption is the "distributed software". Lately all our projects are distributed. Customers are from Europe, USA, Gulf. Developers are working remotely from different areas.
What are the challenges behind such distributed agile work???The answer of this question can be summarized in knowing that agile methods mainly rely on informal processes to facilitate coordination while distributed software development typically relies on formal mechanisms.
Challenges in Agile Distributed Development
- Communication need vs. communication impedance: How can we achieve a balance in formality of communication in agile distributed environments?
- Fixed vs. evolving quality requirements: the Agile relies on ongoing negotiations between the developer and the customer while Distributed Development often relies on fixed, upfront commitments on quality requirements.
- People- vs. process-oriented control: We appreciate the people-orientation the most.
- Lack of cohesion: Generally speaking about the distributed environment, people may feel In distributed development, participants are less likely to perceive themselves as part of the same team when compared to co-located participants. the agile adds some more excitement to it :)

- Process Refactor: Continuous process adjustments instead of following strictly the agile practices. It is also recommended to document the requirements at different levels of formality.
- Knowledge Spreading: the team should share their knowledge regarding different domains(business, code, test cases..etc). Alot of tools were developed to reduce the overhead of knowledge-sharing activities. Code/process Repository is a must. the Wiki also is a very important way to share the How-Tos between members. I can't neglect the Bugzilla with its role in creating database to help teams report issues and assign priorities.
- Short Iterations: any iteration should not exceed 2 weeks. short iterations help to detect any misunderstandings for the project business and prevent any time waste.
- Start with well-understood functionalities: In order to create the best atmosphere for developers there should be a solid sand to start to be familiar with the processes, tools, and the application. this can be some kind different that the agile which advocates the development of features prioritized as critical by the customer.
- Improve Communication: Synchronized work hours are very important for the team. Also try to make the informal communication be done through formal channels. for example, let it through the emails so that it can be archived. In the distributed Projects it is recommended that the project leader/manager should be involved in the communication and the synchronization process than the Agile practice. finally, some daily mechanisms should be done to maintain minimal communication like morning online meeting.
- Building Trust: trust involves both the team and the customers.

1. Ebert, C. and Neve, P.D. Surviving global software development. IEEE Software 18, 2 (Mar./Apr. 2001), 62–69.
2. Highsmith, J. and Cockburn, A. Agile software development: The business of innovation. IEEE Computer 34, 9 (Sept. 2001), 120–122.
3. Matloff, N. Offshoring: What can go wrong? IT Professional (July/Aug.2005), 39–45.
Saturday, May 12, 2007
Web Antivirus
Web Services are increasingly becoming an essential part of your everyday life. How much time you spend surfing the internet pages?
It is sufficient only one visit from you to make the attacker able to detect and exploit a browser
Are the web masters, or the site creators are responsible for this?
The answer is, it is not always the case.
User Contribution
Advertising
Although web masters have no direct control over the ads themselves, they trust advertisers to show non-malicious content. Sometimes, advertisers rent out part of their advertising space; in this case the web master needs to trust the ads provided from a company that might be trusted by the first advertiser. And so on, you may find nested relations which considered as pitfall in the trust relation by making it a transitive one.
Third-Party Widgets
A third-party widget is an embedded link to an external JavaScript or iframe that a web master uses to provide additional functionality to users. Example for this, Google Analytics :)
Webserver Security
Update: Google online security blog, the latest news and insights from Google on security and safety on the internet.
To be more specific how much you feel now that Google is too much involved in your daily routine? Can you imagine your life without Google? your search, your Calendar, your email, your blog, ...etc
Well, it seems that you will look for Google to be your web antivirus. Before you access a page, type the url in google search and pray that you won't get "this site may harm your computer".
you have just to obey, otherwise your PC will be affected.the story begins with researchers from the firm surveyed billions of sites, subjecting 4.5 million pages to "in-depth analysis". Actually they found 450,000 pages guilty.
It is sufficient only one visit from you to make the attacker able to detect and exploit a browser
vulnerability. Therefore, the goal of the attacker becomes identifying web applications with vulnerabilities that enable him to insert small pieces of HTML in web pages.
An example for this is iframes, which can successfully install a malware binary "drive-by-download".Are the web masters, or the site creators are responsible for this?
The answer is, it is not always the case.
User Contribution
Many web sites feature web applications that allow visitors to contribute their own content. This is often in the form of blogs, profiles, comments, or reviews. they usually support only a limited subset of the hypertext markup language, but in some cases poor sanitization or checking allows users to post or insert arbitrary HTML into web pages.
Advertising
Although web masters have no direct control over the ads themselves, they trust advertisers to show non-malicious content. Sometimes, advertisers rent out part of their advertising space; in this case the web master needs to trust the ads provided from a company that might be trusted by the first advertiser. And so on, you may find nested relations which considered as pitfall in the trust relation by making it a transitive one.
Third-Party Widgets
A third-party widget is an embedded link to an external JavaScript or iframe that a web master uses to provide additional functionality to users. Example for this, Google Analytics :)
Webserver Security
The contents of a web site are only as secure as the set of applications used to deliver the content, including the actual HTTP server, scripting applications (e.g. PHP, ASP etc.) and database backends. If an attacker gains control of a server, he can modify its content to his benefit. For example, he can simply insert the exploit code into the web server’s templating system. As a result, all web pages on that server may start exhibiting malicious behavior. Although we have observed a variety of web server compromises, the most common infection vector is via vulnerable scripting applications. We observed vulnerabilities in phpBB2 or InvisionBoard that enabled an adversary to gain direct access to the underlying operating system. That access can often be escalated to super-user privileges which inturn can be used to compromise any web server running on the compromised host. This type of exploitation is particularly damaging to large virtual hosting farms, turning them into malware distribution centers.
Exploitation Mechanisms
A popular exploit we encountered takes advantage of a vulnerability in Microsoft’s Data Access Components that allows arbitrary code execution on a user’s computer.
Typical steps taken to leverage vulnerability into remote code execution:
Detecting Dangerous Pages
Simply, by monitoring the CPU and the processes executed on accessing the page. When some unknown processes are added to the list, this will be a strong sign that a drive-by download has happened.
Google will be more and more involved in our life, it will report to you malicious sites for free....
anyway, it is not a big deal, you can do it yourself for some levels. but there a little bit sophisticated cases when you need multilevel reverse engineering...
source: Google Research Paper
Exploitation Mechanisms
A popular exploit we encountered takes advantage of a vulnerability in Microsoft’s Data Access Components that allows arbitrary code execution on a user’s computer.
Typical steps taken to leverage vulnerability into remote code execution:
- The exploit is delivered to a user’s browser via an iframe on a compromised web page.
- The iframe contains Javascript to instantiate an ActiveX object that is not normally safe for scripting.
- The Javascript makes an XMLHTTP request to retrieve an executable.
- Adodb.stream is used to write the executable to disk.
- A Shell.Application is used to launch the newly written executable.
Detecting Dangerous Pages
Simply, by monitoring the CPU and the processes executed on accessing the page. When some unknown processes are added to the list, this will be a strong sign that a drive-by download has happened.
Google will be more and more involved in our life, it will report to you malicious sites for free....
anyway, it is not a big deal, you can do it yourself for some levels. but there a little bit sophisticated cases when you need multilevel reverse engineering...
source: Google Research Paper
Update: Google online security blog, the latest news and insights from Google on security and safety on the internet.
Wednesday, May 09, 2007
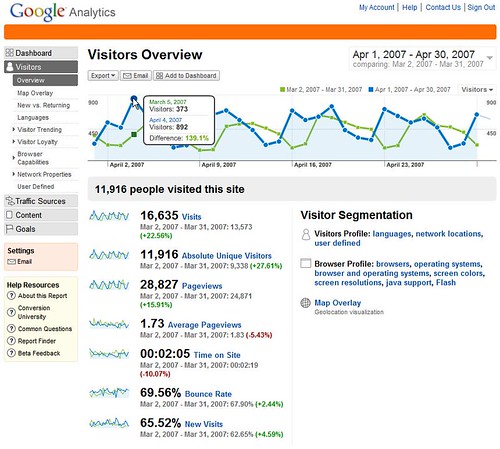
Upgrade your Experience with Google Analytics
Few days ago Google Analytics has released a new version. The new user UI enables easier use of the reports and metrics within the data sets,
NEW:- Email reports and improved clarity of graphs allow users to explore and discover new insights
- Customizable dashboards ensure the right data gets to the right people at the right time
- Plain language descriptions of the data allow users to take action to improve their web site
Attitudes for Creativity
I just remember the Bernards Shaw's quote:" You see things, and you say, "Why?" But I dream things that never were, and I say "Why not?"
I am sure if the creativity can be learned anyway, a lot of people just born to be creative...
maybe someone can see this link listing 9 attitudes for creative people, and tell me if creativity can be learned or not.
the attitudes as listed by the link are as follows:
I am sure if the creativity can be learned anyway, a lot of people just born to be creative...
maybe someone can see this link listing 9 attitudes for creative people, and tell me if creativity can be learned or not.
the attitudes as listed by the link are as follows:
1. Curiosity
"What if?", "Why?", "Why Not?"...
2. Seeing Problems as Interesting and Acceptable
 Creative people see problems as a natural and normal part of life - in fact they often have a fascination with problems and are drawn to them.
Creative people see problems as a natural and normal part of life - in fact they often have a fascination with problems and are drawn to them.
3. Confronting Challenge
Asking ‘how can I overcome this’?
4. Constructive Discontent
Awareness of what’s wrong with the world around, then let it be a motivation to doing something constructive.
Friday, May 04, 2007
The 100 most Influential Personalities

The Saudi monarch Abdullah bin Abdul Aziz was ranked 36 among the 100 most influential personalities on the political level in the world for 2007. The list included personalities from diverse backgrounds, including Sudanese President Omar Al-Bashir, along with Egyptian Islamic preacher Amr Khaled. It was striking absence from the list the name of the American President George Bush, leaving the place for Osama bin Laden and the Pope Benedictos XVI and Al Gore, Leonardo de Caprio and others. For the politicians, the list included the name of the American Secretary of State Condoleezza Rice, and the Supreme Leader of the Revolution, the Iranian Ali Khomini, and Raul Castro, brother of Cuban President, along with the Democrats, the main candidates to the American presidential elections of 2008, Hillary Clinton and Barak Obama, in addition to the Chairperson of the American House of Representatives Nancy Pelosi. The 34/39 former U.S. Vice President Al Gore in the category of "scholars and thinkers," along with the co-founder of Microsoft Paul Allen.
In the category of "heroes and pioneers," the name of the multi-millionaire Warren Bouvet, and French soccer star Thierry Henry and an activist in the issue of Darfur Representative George Cluny. It also named for the founder of the site "youTube" electronic videos on the list and the name of the founder of Apple, Steve Jobs.The journal does not rank such personalities, not necessarily to justify why chosen figures, only saying that it wants to honor the "men and women who change the world using their talents, their authorities or their moralities"
This is a strike to the Egyptian system, choosing Abdullah is an indication of the absence of the Egyptian effect on the middle East, where Egypt has been always the most effective player. Currently, it is really obvious that Saudi Arabia stole this role from Egypt.
We don't forget picking Amr Khaled is also a big strike, there were rumors that Amr Khaled was forbidden from Egypt because of the worry of his effect on the Egyptian people, and he faced a lot of Media battles to deny his effect and his role in the islamic world.
Thursday, May 03, 2007
The BlackWater's Danger
I think the phenomenon of BlackWater is too dangerous concept...
The USA uses these kinds of gangs to fight for them instead of get involved in IRAQ, Afghanistan.
These gangs cannot be punished for war crimes, because they are not nothing actually. they are not a military, nothing except...........
They achieved numerous massacres in IRAQ and Afghanistan, wearing Navy Uniform.
Privatization in Egypt is totally different than privatization all over the world :)...This is about the privatization of war and how that subverts even basic notions of democracy. The blackWater is used as a mirror for "Radical Christian Right".
If we are still not aware of wt does this really mean...then here we are..
Blackwater is also the name of private company, formed by an ex-Navy Seal, which owns the training facility and sells "security" to countries or organization doing business in high-risk areas of the globe.
Blackwater's security services included making available - for a price - a small army of heavily armed, experienced mercenaries with access to their own helicopter gun ships, armored vehicles and war planes.
Some says that in 2006, Blackwater had 2300 soldiers deployed in nine countries with a database of 21,000 additional on-call mercenaries.
Where these soldiers come from?????
There are EX-Special Forces from US and UK. they simply can't find inner peace in thir civilian life, so they looked for wars in other countries (Islamic ones). We don't need to say that they r very cruel, experienced, commandos, seal...etc everythg we may think about.
the BlackWater can defeat a significant number of countries.
Some others confirmed that Blackwater has won - on a sole-source basis - more than $500 million of US government contracts, not including unlisted "black" contracts. In addition to Iraq, Blackwater has contracts for work in the Louisiana flood area and on the Mexican boarder. The total global value of private military security contracts is estimated to be $100 billion and rising.
Aren't these terrorist gangs?
they make me sick, that's enough for now :S
The USA uses these kinds of gangs to fight for them instead of get involved in IRAQ, Afghanistan.
These gangs cannot be punished for war crimes, because they are not nothing actually. they are not a military, nothing except...........
They achieved numerous massacres in IRAQ and Afghanistan, wearing Navy Uniform.
Privatization in Egypt is totally different than privatization all over the world :)...This is about the privatization of war and how that subverts even basic notions of democracy. The blackWater is used as a mirror for "Radical Christian Right".
If we are still not aware of wt does this really mean...then here we are..
Blackwater is also the name of private company, formed by an ex-Navy Seal, which owns the training facility and sells "security" to countries or organization doing business in high-risk areas of the globe.
Blackwater's security services included making available - for a price - a small army of heavily armed, experienced mercenaries with access to their own helicopter gun ships, armored vehicles and war planes.
Some says that in 2006, Blackwater had 2300 soldiers deployed in nine countries with a database of 21,000 additional on-call mercenaries.
Where these soldiers come from?????
There are EX-Special Forces from US and UK. they simply can't find inner peace in thir civilian life, so they looked for wars in other countries (Islamic ones). We don't need to say that they r very cruel, experienced, commandos, seal...etc everythg we may think about.
the BlackWater can defeat a significant number of countries.
Some others confirmed that Blackwater has won - on a sole-source basis - more than $500 million of US government contracts, not including unlisted "black" contracts. In addition to Iraq, Blackwater has contracts for work in the Louisiana flood area and on the Mexican boarder. The total global value of private military security contracts is estimated to be $100 billion and rising.
Aren't these terrorist gangs?
they make me sick, that's enough for now :S
Subscribe to:
Posts (Atom)